Azure Service Tags vs AWS IP Ranges: Complete Guide to Cloud Network Security
Understanding Azure Service Tags and AWS IP Ranges for secure cloud networking and firewall configuration
Published: 2025-10-08
When securing cloud infrastructure, network administrators face the challenge of defining precise firewall rules for cloud services. Both Microsoft Azure and Amazon Web Services provide mechanisms to identify their service IP addresses: Azure Service Tags and AWS IP Ranges. Understanding these tools is crucial for implementing robust network security policies that are both effective and maintainable.
What Are Azure Service Tags?
Azure Service Tags represent a group of IP address prefixes from a given Azure service. Microsoft created this abstraction layer to simplify network security rule creation by providing logical names for collections of IP addresses used by Azure services. Instead of managing hundreds of individual IP addresses, administrators can reference a single service tag that automatically includes all relevant IP ranges.
Azure Service Tags cover a wide range of services including:
- AzureCloud: All Azure datacenter IP addresses
- Storage: Azure Storage service IP addresses
- Sql: Azure SQL Database IP addresses
- AzureKeyVault: Azure Key Vault IP addresses
- EventHub: Azure Event Hubs IP addresses
- ServiceBus: Azure Service Bus IP addresses
Each service tag is region-specific when applicable, allowing for granular control. For example, Storage.WestUS contains only storage service IP addresses in the West US region.
What Are AWS IP Ranges?
AWS IP Ranges provide a comprehensive list of all IP address ranges used by Amazon Web Services across all regions and services. Unlike Azure’s tag-based approach, AWS publishes a complete JSON document containing detailed information about every IP range they use, including the specific service, region, and network border group associated with each range.
The AWS IP Ranges document includes:
- Service identifiers: EC2, S3, CloudFront, Route53, etc.
- Region information: us-east-1, eu-west-1, ap-southeast-2, etc.
- IP version: IPv4 and IPv6 address ranges
- Network border groups: Subset of regions for specific services
- Create date and sync token: For tracking updates
AWS provides both IPv4 and IPv6 ranges, with detailed metadata that allows for precise filtering based on service type, geographic region, and other criteria.
How They Are Used
Azure Service Tags Usage
Azure Service Tags are primarily used in Network Security Groups (NSGs), Azure Firewall rules, and route tables. Administrators can create security rules that reference service tags instead of specific IP addresses:
Source: Any
Destination: Storage.WestEurope
Port: 443
Protocol: TCP
Action: AllowThis rule automatically includes all Azure Storage IP addresses in West Europe, eliminating the need to maintain individual IP address lists. Service tags can also be used in User Defined Routes (UDRs) and Virtual Network service endpoints.
AWS IP Ranges Usage
AWS IP Ranges require more manual processing but offer greater flexibility. Organizations typically download the JSON document and extract relevant IP ranges for their specific use cases. These ranges are then used in:
- Security Group rules
- Network ACL entries
- Route table entries
- Third-party firewall configurations
- Load balancer configurations
The granular data allows for highly specific rules, such as allowing only S3 traffic from the us-east-1 region while blocking other AWS services.
Why They Are Used
Simplified Management
Both systems eliminate the need to manually track and update IP addresses as cloud services expand or change their infrastructure. Cloud providers continuously add new IP ranges as they grow their global footprint, making manual management impractical.
Enhanced Security
By using these official IP ranges, organizations ensure their firewall rules remain current and comprehensive. This reduces the risk of connectivity issues or security gaps that might arise from outdated IP address lists.
Operational Efficiency
Service tags and IP ranges reduce configuration complexity, minimize human error, and accelerate deployment of network security policies. Teams can implement consistent security standards across multiple environments without extensive manual configuration.
Why They’re Better Than FQDNs
Reliability and Performance
While Fully Qualified Domain Names (FQDNs) require DNS resolution, IP-based rules provide direct network-layer filtering. This eliminates DNS lookup latency and removes dependency on DNS service availability. Network equipment can process IP-based rules more efficiently than application-layer FQDN filtering.
DNS Vulnerabilities
FQDNs are susceptible to DNS hijacking, cache poisoning, and other DNS-based attacks. IP-based filtering operates below the application layer, providing protection against these attack vectors.
Firewall Compatibility
Traditional network firewalls and security appliances are optimized for IP address filtering. Many devices have limited or expensive FQDN filtering capabilities, while IP-based rules are universally supported and perform better.
Consistency Across Environments
IP ranges provide consistent behavior across different network configurations, while FQDN resolution can vary based on DNS server configuration, caching policies, and network conditions.
Key Differences Between Azure and AWS Approaches
Format and Structure
Azure Service Tags use human-readable names that abstract underlying complexity, while AWS provides raw IP range data requiring additional processing. Azure’s approach is more user-friendly for basic scenarios, while AWS offers greater flexibility for complex filtering requirements.
Granularity
AWS IP Ranges provide more detailed metadata, including network border groups and specific service breakdowns. Azure Service Tags offer broader categorization with regional variants but less granular service-level detail.
Update Mechanisms
Azure Service Tags are automatically updated in the Azure platform, requiring no action from users. AWS requires organizations to periodically download and process the updated JSON document to maintain current IP range information.
Integration Methods
Azure Service Tags integrate natively with Azure networking services through simple name references. AWS IP Ranges require custom automation or manual processing to extract and apply relevant IP addresses to security configurations.
Access Methods and Update Frequency
Azure Service Tags Access
Azure Service Tags are accessible through multiple methods:
- Azure Portal: Browse available tags in NSG rule creation
- REST API: Programmatic access via Azure Resource Manager APIs
- PowerShell/CLI: Command-line tools for automation
- JSON Downloads: Weekly downloadable files for offline processing
Microsoft updates service tags automatically within the Azure platform and publishes downloadable JSON files weekly, typically on Mondays. Changes are reflected immediately in Azure services, with external downloads following shortly after.
AWS IP Ranges Access
AWS IP Ranges are available through:
- Direct Download: https://ip-ranges.amazonaws.com/ip-ranges.json
- SNS Notifications: Subscribe to updates via Simple Notification Service
- API Integration: Automated download and processing systems
- Third-party Tools: Various community and commercial tools for processing
AWS updates their IP ranges document as needed, typically weekly but sometimes more frequently during rapid infrastructure expansion. The document includes a sync token and create date for tracking changes and ensuring current data usage.
Best Practices and Implementation
Automation Strategies
Organizations should implement automated systems to consume these IP ranges, whether through Azure’s native integration or custom AWS processing pipelines. Regular updates ensure security policies remain effective as cloud infrastructure evolves.
Testing and Validation
Before implementing IP range-based rules in production, thorough testing in development environments helps identify potential connectivity issues and ensures business applications continue functioning correctly.
Monitoring and Maintenance
Establish monitoring systems to detect when IP range updates might affect existing connections. This is particularly important for AWS implementations where manual processing introduces potential lag time between updates and implementation.
Native Cloud Firewalls Integration
While Azure Service Tags and AWS IP Ranges integrate seamlessly with native cloud firewalls, the cost implications can be significant for organizations. Native cloud firewalls are built-in solutions provided directly by cloud service providers, offering tight integration with their respective ecosystems.
Cost Considerations
Native cloud firewall solutions, while integrated, come with substantial costs:
- Azure Firewall: Starts at approximately $1.25/hour (~$912/month) for the Standard tier, plus $0.016 per GB of data processed
- AWS Network Firewall: Costs around $0.395/hour (~$289/month) per firewall endpoint, plus $0.065 per GB of data processed
- Additional charges: Both platforms charge extra for high availability, premium features, and increased throughput capacity
For a typical SMB processing 1TB of data monthly, these costs can easily exceed $1,500-2,000 per month across multiple environments.
Revolutionary Integration: Enforza’s Multi-Cloud Approach
Enforza has pioneered the world’s first comprehensive integration of both Azure Service Tags and AWS IP Ranges into a unified cloud security platform. This groundbreaking approach eliminates the complexity and cost barriers traditionally associated with multi-cloud network security management.
How It Works
Enforza’s platform automatically synchronizes with both Microsoft’s weekly Service Tag updates and AWS’s dynamic IP range publications, providing real-time access to official cloud service IP ranges through a single interface:
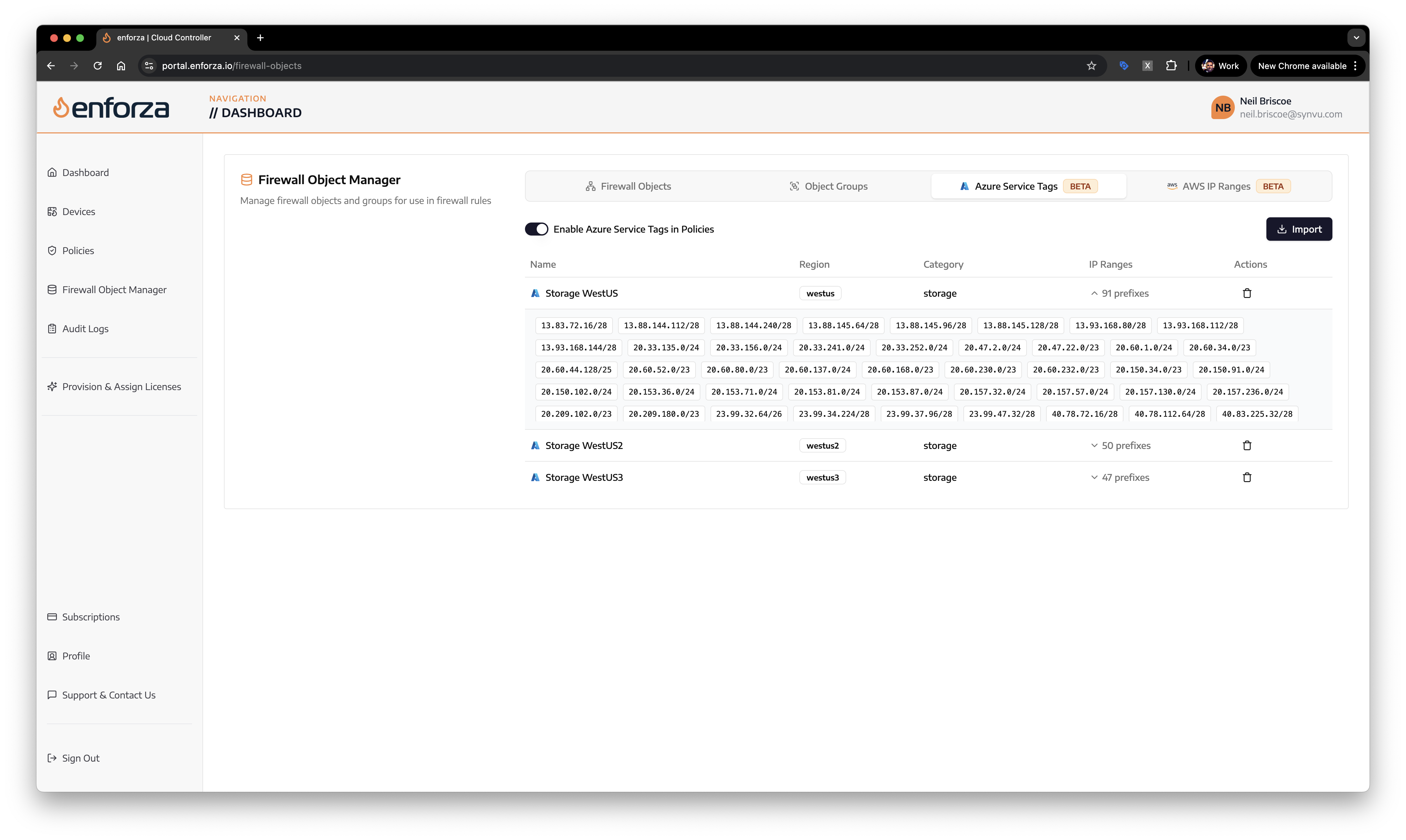
Multi-cloud firewall objects management with unified Azure and AWS integration
Unified Management Interface
The platform provides administrators with intuitive selection and management of both Azure Service Tags and AWS IP Ranges from a single dashboard, eliminating the need for separate tools or manual JSON processing:
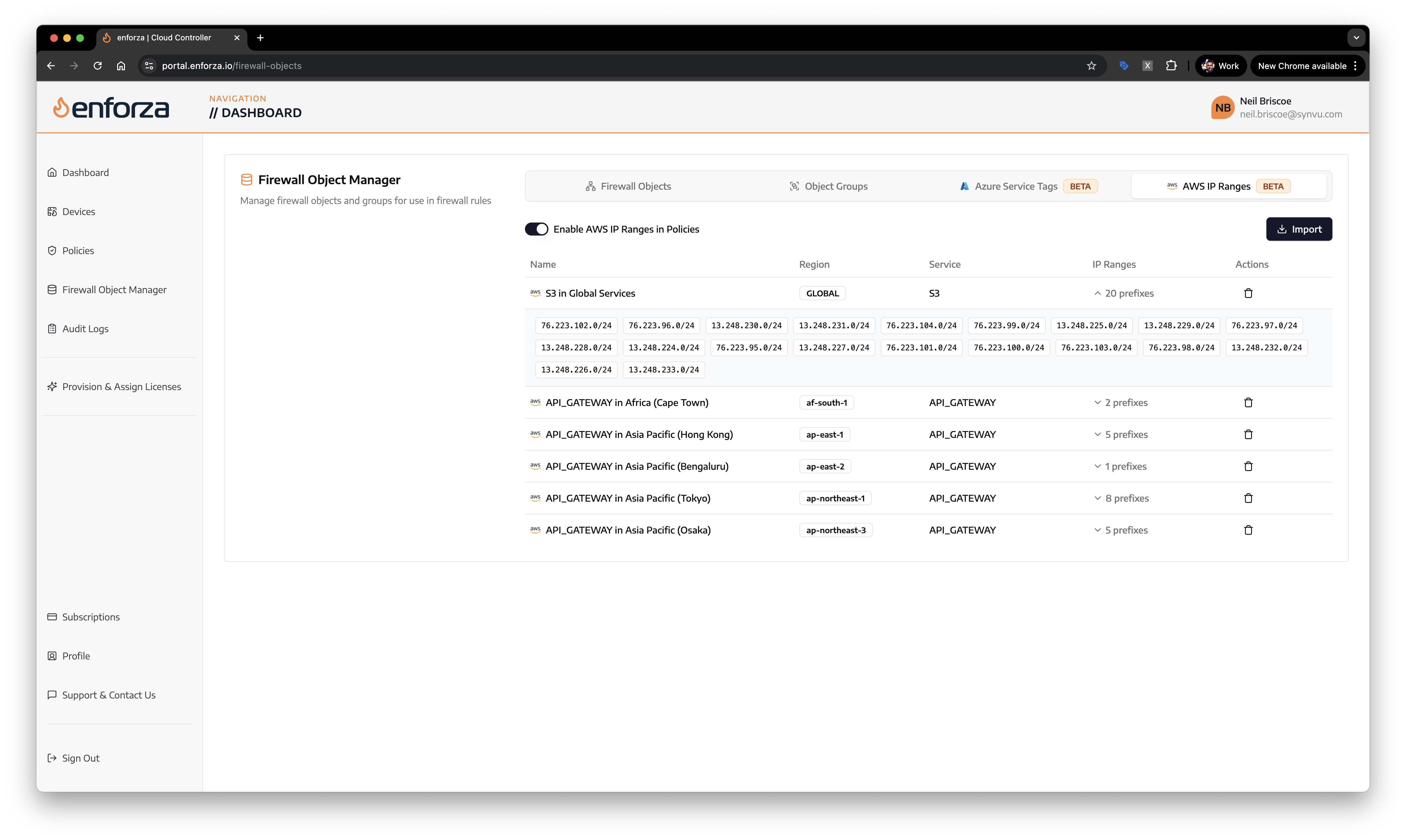
Seamless policy creation with both Azure Service Tags and AWS IP Ranges
Automatic IP Resolution
When creating firewall policies, Enforza automatically resolves Service Tags and IP Ranges to their actual IP prefixes, ensuring rules remain current and comprehensive without manual intervention:
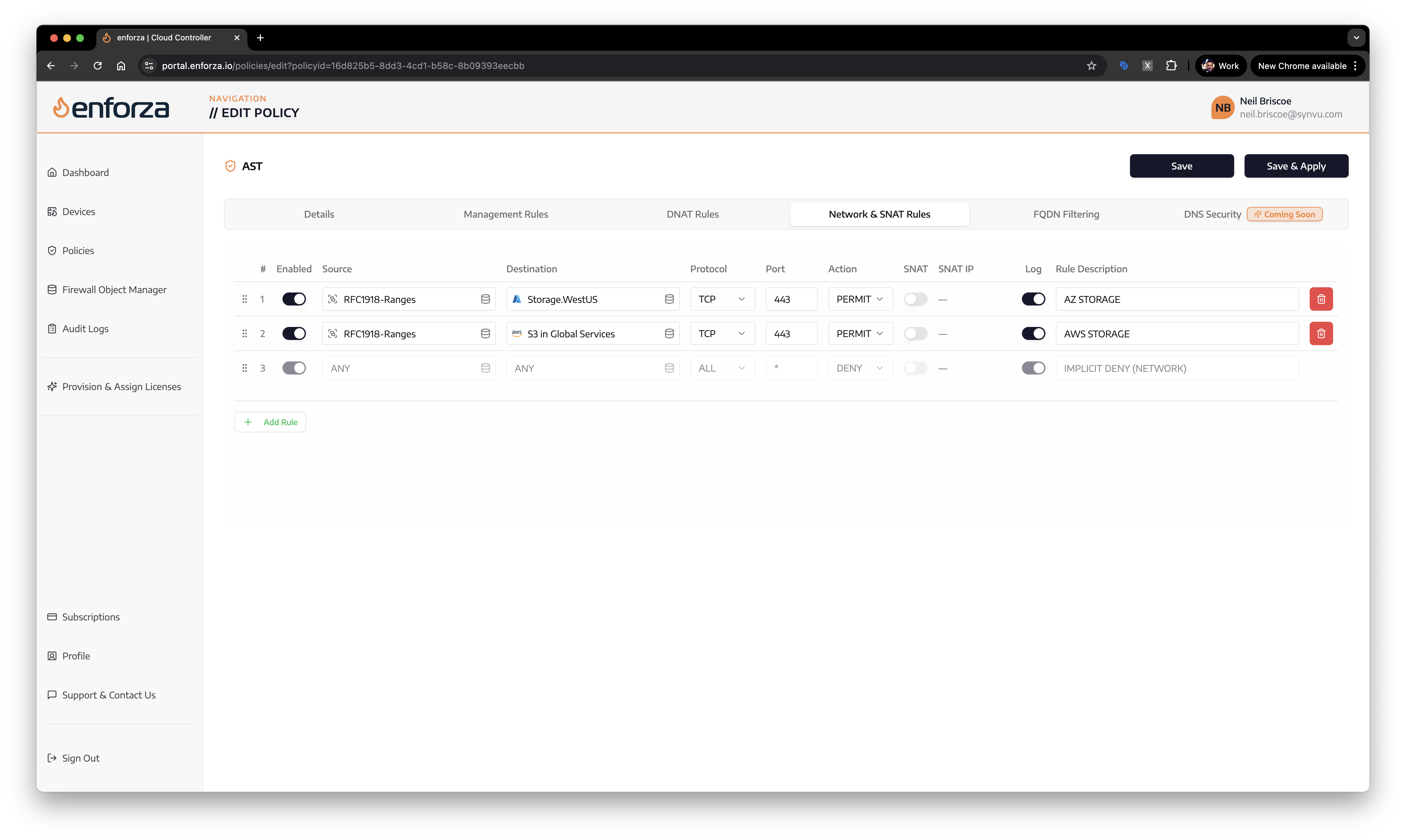
Real-time IP prefix resolution for accurate firewall rule generation
Why It’s Brilliant
This integration delivers unprecedented value:
- Up to 80% Cost Savings: Eliminate expensive native cloud firewall licensing and data processing fees
- Single Pane of Glass: Manage multi-cloud security policies from one unified interface
- Zero Vendor Lock-in: Deploy consistent policies across AWS, Azure, and GCP environments
- Automatic Updates: Stay current with cloud provider IP changes without manual intervention
- Enhanced Security: Leverage official cloud provider IP ranges with enterprise-grade policy management
By combining the best of both Azure and AWS approaches with intelligent automation, Enforza enables organizations to implement sophisticated multi-cloud security policies at a fraction of traditional costs, while maintaining the flexibility and control needed for modern cloud environments.
Conclusion
Both Azure Service Tags and AWS IP Ranges serve the critical function of enabling secure, manageable network policies for cloud services. Azure’s approach prioritizes ease of use and automatic updates, making it ideal for organizations heavily invested in the Azure ecosystem. AWS provides more detailed control and flexibility, suitable for complex multi-cloud environments requiring granular network segmentation.
Understanding and properly implementing these tools significantly improves cloud security posture while reducing administrative overhead. As cloud infrastructure continues expanding globally, leveraging official IP range information becomes increasingly important for maintaining robust, scalable network security policies that adapt automatically to infrastructure changes.
The choice between approaches often depends on existing infrastructure, team expertise, and specific security requirements. Regardless of platform, moving away from manual IP address management toward these official, automated solutions represents a critical step in mature cloud security practices.