Azure Secure NAT Gateway
Default outbound access is ending.
In March 2026, Azure is removing default internet access for VMs (we think it's a good thing - read here),
but it could break your services, pipelines, scaling-groups, and leave you in a mess.
The Problem
What's changing?
Currently, Azure assigns a default public IP for outbound internet access from VMs. This simplifies workflows by enabling VMs to communicate with external services (e.g., APIs, websites) without extra configuration. However, starting March 2026:
- Default public IPs will no longer be assigned to new or existing VMs.
- Outbound traffic will require explicit configuration using a NAT Gateway, Azure Firewall, Load Balancer, or a dedicated public IP.
This change impacts both cost and ease of use, especially for workloads that rely heavily on external internet connectivity.
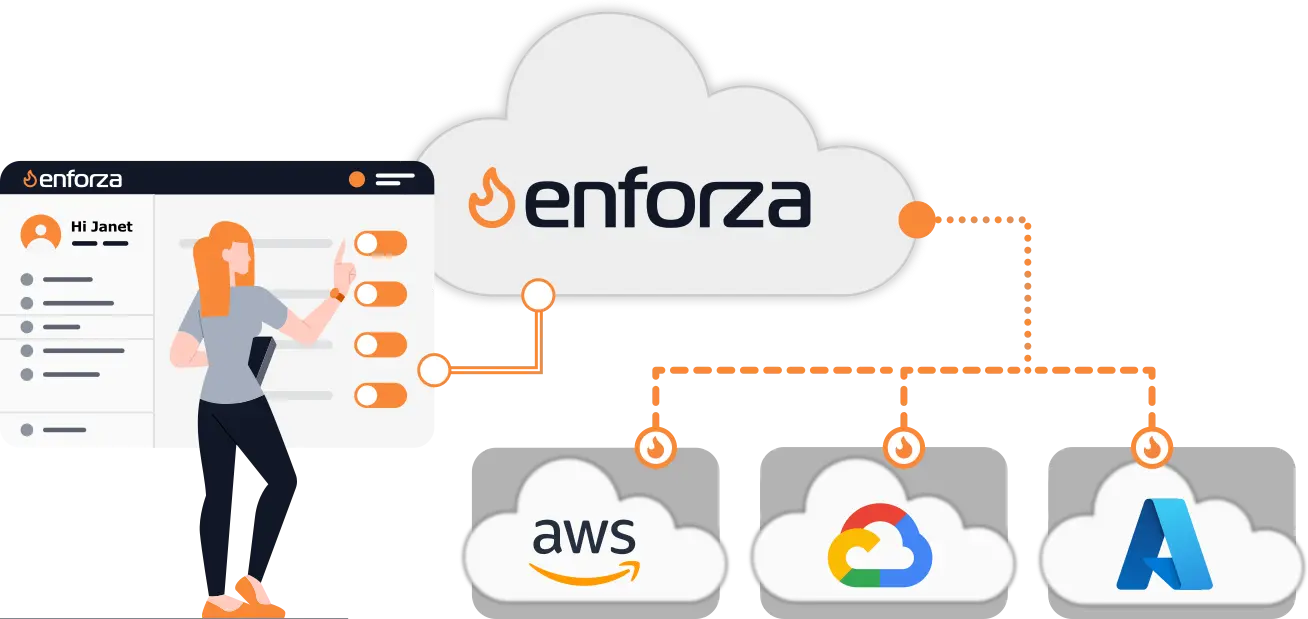
The Solution
Take control before the change
Native Azure NAT Gateways just perform NAT. No visibility, no control, no firewalling, no FQDN filtering. They also incur data processing charges.
Native Azure Firewalls are expensive and not entirely intuitive. They also incur data processing charges.
enforza delivers egress NAT, firewalling, and FQDN filtering in one unified, cloud-managed appliance — eliminating the need for multiple Azure services, with no data processing charges.
Regain control with enterprise-grade egress security whilst gaining significant cost savings, and visibility you didn't have before.
- Deployable in Minutes, with Ease
- Secure your perimeter in 3 easy steps. Deploy VM. Install agent. Push policies from the enforza Cloud Controller to your gateway(s).
- Control NAT
- Replace Azure NAT Gateway’s “NAT everything” behavior with granular, policy-driven control over which traffic is allowed to egress – by IP, port, protocol.
- Save up to 80%
- Eliminate Azure’s opaque egress data processing charges by switching to enforza’s flat-rate subscription — saving up to 80% with transparent, predictable billing
- Unified Edge
- Consolidate Azure NAT Gateway, NSGs, and Firewall into a single, lightweight enforza appliance that handles NAT, firewalling, and FQDN filtering — no complex setup required
- Gain Visibility
- Monitor every outbound connection in real-time — including destination, hostname, location, and source device — to uncover misconfigurations or unexpected traffic patterns
- FQDN Filtering
- Enforce allow/block policies at the FQDN level without relying on DNS proxying or deploying agents — ideal for SaaS filtering, compliance, and secure internet access
- Multi-Cloud Ready
- Deploy across multiple clouds (Azure, AWS, GCP) with consistent policy enforcement and centralized management — no lock-in to a single provider’s ecosystem
FAQs
Can’t find the answer you’re looking for? Drop us a message here and we'll get back to you.
- If I do nothing, what happens?
- Basically, headaches! All new VMs will not have access to the internet which may cause surprises especially if you are running automation and pipelines that are in place. Scale-sets that are dynamically changing may have issues and cause service outages. Redeploying of VMs will have no internet access or public IP addresses, therefore, unable to manage them remotely.
- Is the enforza virtual appliance just a straight Azure NAT Gateway replacement?
- If you want it to be. However, enforza virtual appliances act as a more configurable NAT gateway, but with added stateful firewall capability and FQDN filtering which Azure NAT Gateways cannot do. Can you choose to use enforza as just the NAT Gateway capability and you still save significant amounts by remove the data processing charges.
- How much can I save using enforza gateways compared to Azure NAT Gateway or Azure Firewall?
- You can save up to 80% by replacing your Azure NAT Gateways or Azure Firewalls... or more if you leverage the unified capability of enforza (it does it all). Use our calculator, below, to give an estimate on savings based upon 1 Azure NAT Gateway or Firewall. You will save significantly more by utilising centralised egress across your VNETs - i.e in a hub/spoke topology.
- How much can I save by provisioning enforza gateways?
- You can save up to 80% by replacing your Azure NAT Gateways or Azure Firewalls... or more if you leverage the unified capability of enforza (it does it all). Use our calculator, below, to give an estimate on savings based upon 1 Azure NAT Gateway or Firewall. You will save significantly more by utilising centralised egress across your VNETs - i.e in a hub/spoke topology.
- How easy is it to deploy enforza?
- We deliberablely designed the whole platform to be easy. Deploy a VM (or VMs) in your Azure environment, install the agent (transforms into a hardened security appliance and registers to your account), create a policy and deploy it. Takes less than 5 minutes to secure your environment.
- How can I evaluate enforza in my environment?
- Again, we designed the provisioning to be easy, frictionless, and low-risk. You provision an enforza virtual appliance in your environment, install the agent, deploy a policy. Then you can change the default/interet route in your UDR (Azure route table) to point to the IP of the new gateway. All traffic will be forwarded through the enforza NAT Gateway/Firewall at this point. If you need to change back, it is a simple UDR change again that takes seconds.
- What visibility with enforza give me?
- enforza sees every outbound connection allowing you to control traffic. enforza allows you to see standard firewall rule hits (with packet forensics if you wish), FQDN rules and decision outcomes, as well as analytics. Azure NAT Gateway will not give you this visibility, so if you chose to use enforza as the NAT Gateway capability, you will see every session allowing you to make decision on defining your security policy.












Ditch the data processing charges.
Gain full control of your outbound traffic — in any cloud or on-prem.